

New research by Marsh McLennan has revealed a direct link between key cybersecurity controls and a reduced chance of cyber incidents.
The report found that evaluating the relative effectiveness of each cybersecurity control enables organizations to allocate resources to those that provide the best protection, which allows them to better position their risk with insurers, while also helping them build their cyber resilience more confidently.
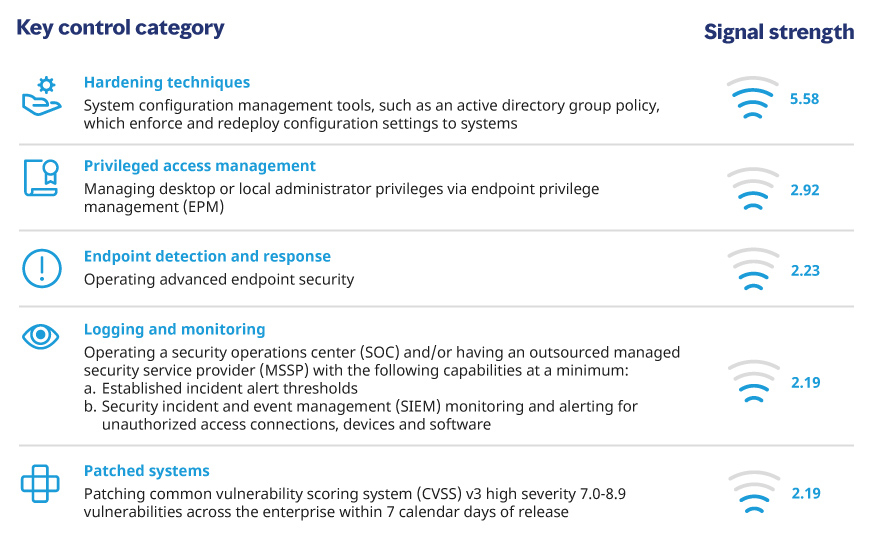
Automated hardening techniques were found to have the greatest ability to decrease the likelihood of a successful cyberattack.
According to the report, organizations that use such techniques, which apply baseline security configurations to system components like servers and operating systems, are nearly six times less likely to have a cyber incident than those that do not.
Marsh McLennan stated that this finding was particularly surprising, given that the three controls most frequently recommended by insurers have been endpoint detection and response (EDR), multifactor authentication (MFA), and privileged access management (PAM).
The analysis also showed that MFA only works when it is in place for all critical and sensitive data, all remote login access, and administrator account access. Organizations with such broad implementation are 1.4 times less likely to experience a successful cyberattack than those that do not, the report noted.
Meanwhile, patching high severity vulnerabilities across the enterprise within seven days of the patch’s release was deemed the fourth most effective control. It was found to decrease an organization's probability of experiencing a cyber event by a factor of two. However, it has the lowest implementation rate among organizations studied, at only 24%.
For the report, Marsh McLennan paired its proprietary dataset of cyber claims with results from Marsh Cybersecurity Self-Assessment (CSA) questionnaires to calculate and assign a “signal strength” to each control.
It specifically focused on the cyber capabilities, tools, and implementation techniques that fell within the 12 key control categories commonly required by cyber insurers.
Among these, the top five controls determined to be most effective were: hardening techniques, privileged access management, endpoint detection and response, logging and monitoring, and patched systems.
“All of the key controls in our study are well-known best practices, commonly required by underwriters to obtain cyber insurance,” said Tom Reagan, US and Canada cyber practice leader at Marsh. “However, many organizations are unsure which controls to adopt and rely on expert opinions rather than data to make decisions.”
Reagan described the research as a way to provide organizations with the data needed to more effectively direct cybersecurity investments, “which in turn helps favorably position them during the cyber insurance underwriting process.”
“It is another step toward building not only a more resilient cyber insurance market, but also a more cyber resilient economy,” he added.
Additional insights from the research will be used as part of a forthcoming cyber event attritional loss model aimed at informing insureds of potential losses they could suffer, as well as the potential savings benefit from increasing their cybersecurity posture.
“Marsh McLennan launched the Cyber Risk Analytics Center in late 2021 with the goal of helping organizations make smarter investments in the ways they identify, prepare for, and recover from cyber risk,” said Scott Stransky, leader of the Marsh McLennan enterprise-wide resource. “This groundbreaking report will be indispensable to Marsh McLennan clients as we work together to build society’s resilience to this critical and costly risk.”
What are your thoughts on this story? Feel free to comment below.
